
Information Security Governance
What is Information security governance?
Information security governance is a system that directs and controls IT security. This is not the same thing as IT security management, however. IT security management is concerned with making decisions to mitigate risks, while governance determines who is authorized to make those decisions. Generally speaking, governance lays out the accountability framework and provides oversight to ensure that risks are mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies, but governance ensures that security strategies are aligned with business objectives and consistent with regulations.
Why your organization needs Information security governance?
How to create an effective information security governance?
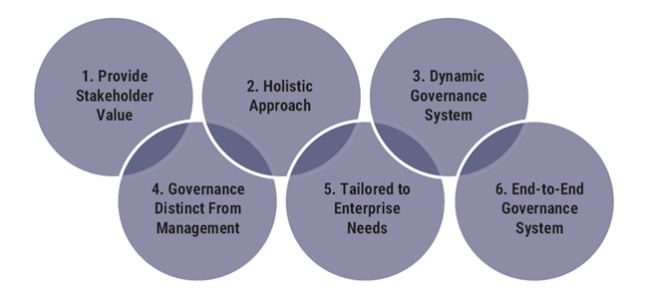
- A comprehensive information security strategy linked with business objectives, as well as security policies that address each aspect of strategy, controls, and regulation
- A complete set of standards for each policy to ensure that procedures and guidelines comply with the policy
- An effective cybersecurity policy, including an organizational structure with sufficient authority and adequate resources to enforce the policy.
- An institutionalized metrics and monitoring processes to ensure compliance, provide feedback and provide the basis for appropriate management decisions.
This can all get very technical and confusing, but that’s why we’re here to help you through it.
Schedule a consultation and we’ll work with you on creating, improving, or just reviewing your businesses’ information security governance system.
About the Author: Jenny Jo
Headquarters
Empire State Building
Network Operation Center (NOC) Office
Powered by Ultratek Computers & Communications | Created by Top Web Designer | Marketed by Tri-State Web Marketing | Managed by MJJT Consultants
Copyright © 2019 Secured Transactions. All Rights Reserved.
 212 868-0688
212 868-0688

